I have automated the change that LastPass made to their fill-in process. It will decrypt credentials for websites listed in the 'login_urls' resource.
This was working as of December 2014. LastPass may have changed things up again since then, but they probably can't do anything to make app-fill work securely in pre-5.0 devices (which currently accounts for >95% of devices)
I am no longer maintaining this application as I believe it has served its original purpose: to publicise the clipboard vulnerability in Android password managers.
If anybody would like to take over, open an issue and I will be happy to link to their forked repo in this README.md.
Thanks to everybody who helped spread the word!
LastPass has changed their javascript, ClipCaster no longer gets the credentials. An explanation of the changes (and a demonstration on how to bypass them) can be found here: LastPass' attempt at client-side Android encryption with JavaScript: a breakdown. A copy of the new javascript can be found at https://raw.githubusercontent.com/activems/clipcaster/master/js_dumps/lastpass_output_v3.js.
If anyone would like to automate that and implement it in ClipCaster I would be very happy to merge it :)
ClipCaster is a free and open source proof of concept app that shows how any installed app can read passwords when they're used from password management applications.
Thanks to Dan Goodin from Ars Technica for the chance to explain the issue. The resulting article: Using a password manager on Android? It may be wide open to sniffing attacks
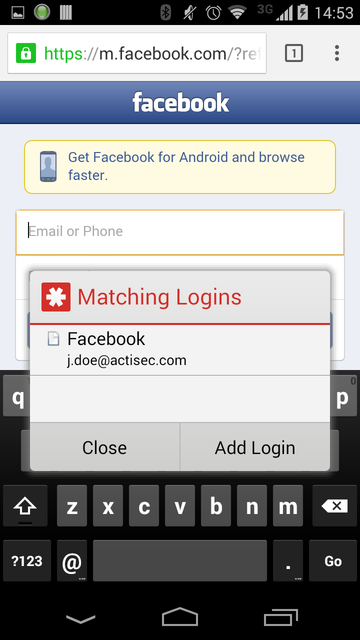
LastPass presents credential options when it detects a fillable page
Once credentials are chosen, we have them (see notification bar)
We post them as a notification (old versions of LastPass, see update at the top)
ClipCaster is an implementation of the concept in "Hey, You, Get Off of My Clipboard - On How Usability Trumps Security in Android Password Managers" (http://fc13.ifca.ai/proc/4-2.pdf), specifically for the LastPass/Chrome combination.
I've written a couple of blog posts with more details:
How Android password managers fall prey to the clipboard vulnerability
LastPass' attempt at client-side Android encryption with JavaScript: a breakdown
Hopefully this app will show people that by using these applications they are trading their security for usability. This decision is every individual person's to make, and it should be an informed one.
If you would like to contribute, make an issue (or just do the modifications and make a pull request)
As stated earlier, this is not an original exploit. Regardless, we disclosed our application to LastPass and they responded with the following:
This is a well-known issue, but is no worse than users manually copying and pasting credentials. App fill just automates the copy/paste process to provide a much better UX. Unfortunately, until Android introduces a secure clipboard feature, or allows direct integration with apps and the browser, there isn't much we can do about this in our app. In the meanwhile, we would recommend that users concerned about this issue not use apps they do not trust, not install apps from untrusted sources, or use the LastPass keyboard/input method to fill logins directly, which does not use the clipboard.
All source code written for the ClipCaster app is licensed under the FreeBSD license, as written below.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The views and conclusions contained in the software and documentation are those of the authors and should not be interpreted as representing official policies, either expressed or implied, of the FreeBSD Project.